The Next Breach Won’t Be a Hack: It’ll Be a Deepfake. The $1.5 Billion Identity Crisis.

TL;DR
- The Threat Shift: The primary vector is no longer code injection or malware; it’s identity injection—AI-driven deepfakes impersonating executives and key personnel.
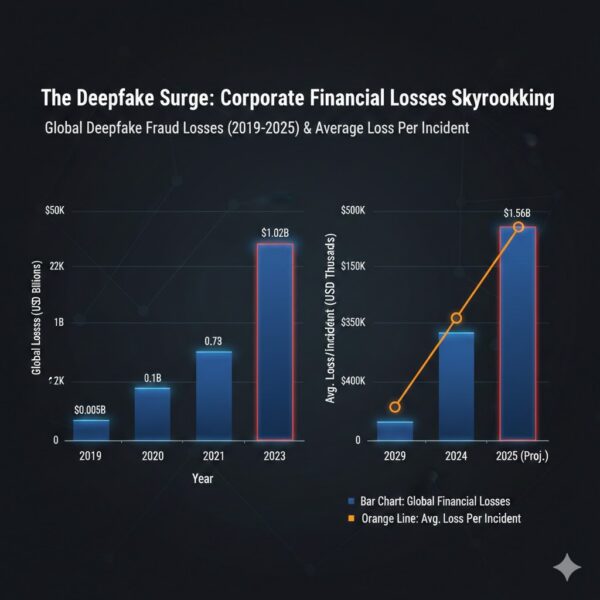
- The Cost: Global deepfake fraud losses surged past $1.56 billion in 2025. Individual corporate incidents now average nearly $500,000.
- The Failure Point: Traditional defenses like Multi-Factor Authentication (MFA) and basic liveness detection are consistently being bypassed by real-time synthetic media attacks.
- The Mandate: You must upgrade from network defense to Identity Integrity Architecture using specialized, multi-modal, AI-native detection technology.
- Next Step: The time for awareness is over. Request a private demo of Blackfence by Saptang Labs to deploy the next generation of identity defense and quantify your current vulnerability.
- The Existential Threat: Why Your Perimeter is Already Compromised
We are entering a new era of cyber risk where the threat actor isn’t breaking into your system; they are logging in as your CEO. The era of the network intrusion is giving way to the age of identity injection.
In January 2024, a finance executive at a British engineering firm authorized a transfer of nearly $25 million across 15 transactions. The trigger? A sophisticated video call involving the deepfaked images and voices of familiar colleagues. This wasn’t a phishing email or a zero-day exploit; it was the exploitation of human trust, weaponized by generative AI.
This alarming event is not an outlier. Industry data confirms that 85% of financial professionals now view deepfake scams as an ‘existential’ threat to their organization’s financial security. The threat is real, immediate, and targets the most valuable asset in the modern enterprise: trust.
Your urgent focus must shift from securing the firewall to verifying the absolute integrity of every digital face and voice that touches your financial, HR, and IT systems.
- The Anatomy of a Bypass: How Deepfakes Defeat Modern Security
The challenge with deepfakes is that they exploit security controls designed for the previous generation of threats. They don’t steal credentials; they steal the authentication moment.
Bypassing Biometrics and MFA
Biometric verification, password resets, and high-value transactions often rely on a single moment of liveness validation (e.g., blink, head turn, or voice match). Attackers are bypassing these checks through two primary methods:
- Injection Attacks: Fraudsters are using deepfake tools to generate hyper-realistic video or audio and “inject” it directly into the verification system’s stream, bypassing the camera/microphone capture entirely. These injection attacks surged 40% year-over-year, and deepfakes now account for one in five biometric fraud attempts.
- Voice Cloning at Scale: With modern AI tools, a compelling voice clone can be generated from as little as three seconds of publicly available audio (e.g., corporate earnings calls, marketing videos). This allows attackers to defeat voice-based authentication and escalate Business Email Compromise (BEC) into Voice-Based Executive Fraud.
The core weakness is this: traditional systems ask, “Do the credentials match?” The AI threat asks, “Is this person real?”
Visualization of the Crisis: Financial Impact
The escalating financial consequences demand board-level attention. The following data illustrates the urgency of investing in deepfake defense:
- The Executive Strategy: From Reactive Compliance to Proactive Integrity
This is not a technology problem for the IT team; it is a fundamental governance challenge for the C-Suite. The strategy must be unified, blending technology investment with human resilience.
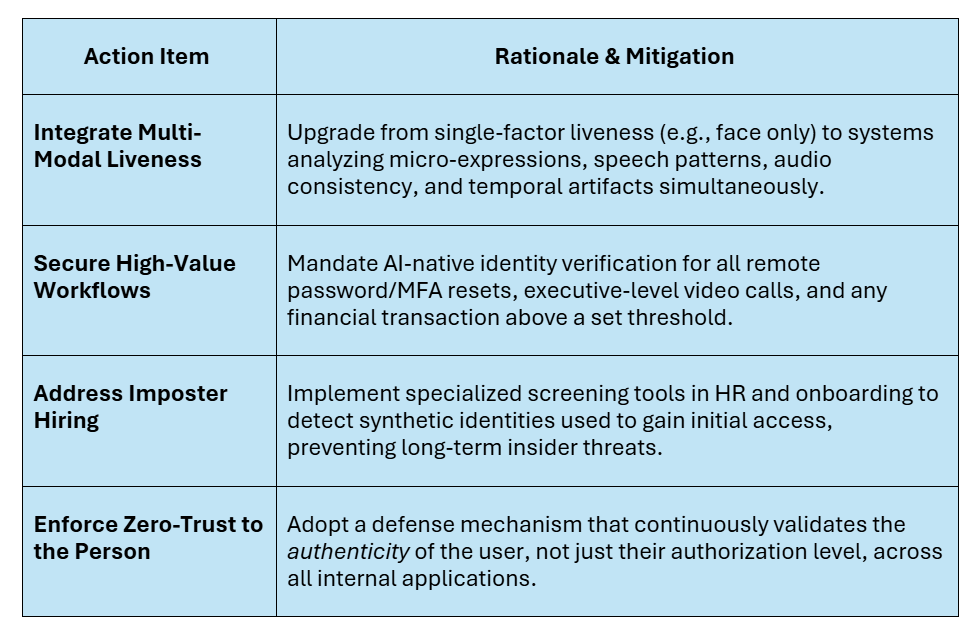
- The CISO’s Operational Roadmap
The CISO mandate is to build an Identity Integrity Architecture that assumes the identity layer is the highest-risk perimeter.
- The CEO’s Governance Mandate
The CEO’s role is to ensure institutional immunity and reputation resilience.
- Financial Integrity Protocol: Implement a mandatory, non-negotiable out-of-band verification protocol for all high-value transactions. This means never trusting a video or voice call alone; use a predetermined, non-digital codeword or callback on a separate, trusted device.
- Reputation Defense Readiness: Collaborate with legal and communications teams to develop rehearsed incident response playbooks for executive impersonation or brand manipulation events.
- Invest in Future-Proofing: Allocate budget to specialized, third-party AI detection platforms. This is not a capital expense; it is insurance against systemic fraud and irreversible reputation loss.
- The Solution: Blackfence’s AI-Native Identity Integrity
Traditional security is reactive; Blackfence is predictive.
At Saptang Labs, we recognize that to defeat an AI-generated threat, you need a specialized, dedicated AI defense. Blackfence is engineered to establish and maintain Identity Integrity across your enterprise:
- Passive, Multi-Layer Liveness: Blackfence doesn’t ask the user to blink or turn their head. It passively analyzes hundreds of microscopic cues—such as natural skin texture, light refraction in the eye, and subtle lip-to-speech synchronization—to detect the presence of synthetic media in real-time.
- Acoustic Fingerprinting: Our system builds a unique acoustic fingerprint for high-value executives, instantly flagging audio streams that are “too clean,” lack ambient noise, or show inconsistencies indicative of voice cloning.
- Seamless Integration: Blackfence is designed for minimal friction, integrating easily with your existing Identity and Access Management (IAM) suite and collaboration tools to protect the moment of verification, without disrupting workflow.
The threat landscape has evolved. Your defense must, too. Blackfence moves your security posture from simply managing access to guaranteeing authenticity.
Next Step: The Only Proof is Real-World Performance
Waiting for the next breach is no longer acceptable risk management. The next fraud attempt is likely already underway, disguised as a trusted voice or a familiar face.
Schedule a private, 15-minute demonstration of Blackfence’s Real-Time Detection Engine. See exactly how quickly and easily modern deepfakes compromise the security measures you rely on today—and the surgical precision with which Blackfence stops them.
[Book Your BlackFence Demo Today] | blackfence.saptanglabs.com
FAQ
Q1: Isn’t this just a sophisticated phishing problem?
Ans: No. Phishing targets the link; deepfakes target the identity itself. They bypass all traditional phishing education and technological controls that rely on visual/aural cues of legitimacy. This is identity injection, not simple social engineering.
Q2: Does our current biometric/Liveness Detection solution cover this?
Ans: Highly unlikely. Most legacy biometric systems are trained on basic 2D and 3D spoofing. They are vulnerable to camera injection attacks and cannot reliably detect AI-generated synthetic media, especially when customized for a high-value target.
Q3: What is the primary financial risk for my business today?
Ans: Immediate wire fraud/transfer authorization fraud, averaging nearly $500,000 per incident, and long-term reputational damage leading to loss of customer and investor trust.
Q4: How quickly can Blackfence be deployed in a corporate environment?
Ans: Blackfence is designed for rapid integration into existing enterprise communication and identity workflows (IAM/SSO). Our implementation typically takes days, not months, allowing for immediate protection of your most vulnerable high-value assets.
Q5: Is this a matter for the CISO or the CEO/Board?
Ans: Both. The CISO owns the defense technology and architecture. The CEO/Board owns the residual risk; the potential for multi-million dollar fraud and irreparable brand damage. This requires joint, prioritized strategy and investment.
You may also find this helpful: Digital Trust Is the New Currency: Why Boards Must Treat Cybersecurity as ESG








